Attack Surface Discovery
Find and protect unknown assets across your attack surface with automated, proactive asset discovery.
Automated attack surface discovery
You can't protect what you don't know about. That’s why attack surface management begins with asset discovery. Intruder helps you discover assets across your entire attack surface, including new cloud services, subdomains, login pages, APIs, exposed services, open ports, and more.

Trusted by thousands of companies worldwide































































Close hidden gaps in your attack surface
From related domains and subdomains to logins and APIs, Intruder continuously monitors for assets that are easy to lose track of but can create exploitable gaps in your attack surface. Scan newly discovered assets to check for 1,000+ attack surface issues that other vulnerability scanners miss.

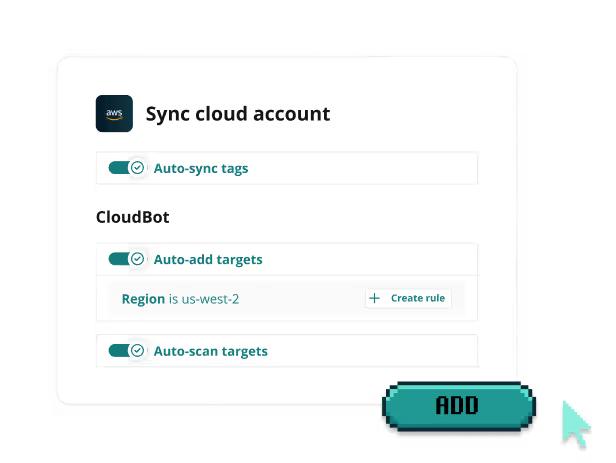
Proactive cloud attack surface discovery
Integrate Intruder with your cloud accounts to automatically discover services as soon as they’re exposed. With automated vulnerability scans triggered by any changes, Intruder ensures you can quickly identify and resolve risks in your cloud environment.
Continuously monitor your network for changes
Get continuous visibility of your perimeter. Intruder’s daily network scans show you active and unresponsive targets, expiring certificates, and the ports and services you expect—and, more importantly, those you don’t expect—to be exposed to the internet.

What is attack surface management?
Learn how to manage and protect your attack surface in our essential guide.


Read our reviews on G2.com





An attack surface is the sum total of all possible paths that can be used to exploit a computer system or network.
More specifically, your external attack surface refers to all the services and systems that can be accessed from the internet. This attack surface changes continuously over time, and includes digital assets that are on-premises, in the cloud, in subsidiary networks, and in third-party environments.
When a new vulnerability is discovered in software deployed on your perimeter, Intruder scans your systems and alerts you automatically. Learn more.
Cloud sync automatically adds new external IP addresses or hostnames in your cloud accounts as Intruder targets. You can enable Intruder to automatically scan new targets as they are added, and create rules to control what’s imported. Head to our help article to learn more.
Intruder’s Rapid Response is manually carried out by our security team to check for the latest critical weaknesses hitting the news, including some that our scanners don't have checks for yet or ones that are better detected by a person. When a threat is identified, we'll scan your systems and notify you if we suspect that any could be affected. We will also send you an advisory with further details and recommendations.
The process of external attack surface management can be summarized as follows:
- Discover and map all your digital assets with asset discovery
- Ensure visibility and create a record of what exists
- Run a vulnerability scan to identify any weaknesses
- Automate so everyone who creates infrastructure can do so securely
- Continuously monitor as new infrastructure and services are spun up
We continuously monitor for APIs related to your live targets using automated domain detection tools. This is currently only available for targets hosted in AWS. Learn more.
Once a week, we will run an automatic scan on all your targets to check for any subdomains that have not yet been added to the portal. Learn more.
When you add a target, we'll check for any related domains that have not yet been added to the portal.
For example, if you have added exampletest.com, we might return exampletester.com or exampletest.co.uk. Read more.




