Automated Penetration Testing
Intruder is an automated vulnerability scanner that finds cyber security weaknesses in your digital infrastructure, to avoid costly data breaches.
Join thousands of companies worldwide protecting their attack surface































































What is automated penetration testing?
Well, yes, sort of! In reality penetration tests involve a range of activities, some of which are manual and some of which can and should be automated. For example, when guessing passwords, a human tester might look at the individuals in a company, and tailor some of their guesses based on birthdays or pets’ names found online; they might even manipulate the company name or office address in the hope it might yield something interesting. However, when it comes to detecting known software flaws – like a server that’s missing security patches, common passwords, or unintended exposure to the internet – this can and should be automated. The tools that find these flaws are actually used by penetration testers, and so are sometimes called automated pen-testing tools, or online penetration testing tools, but are most commonly known as vulnerability scanners.
Historically, penetration tests were usually carried out once or twice per year. However, as the prevalence of automated attacks increases, businesses can no longer afford to rely on one or two check-ups per year. As a result, they are looking for more automated penetration testing tools (which we now know are also called vulnerability scanners). Intruder is an example of a vulnerability scanner, offering year-round protection from opportunistic attackers.
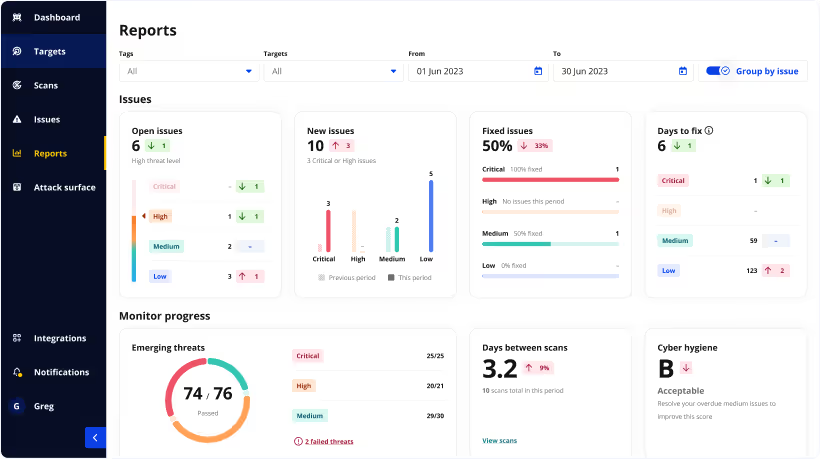
Online penetration testing tool to detect the latest weaknesses
What's more, Intruder includes Emerging Threat Scans, which proactively check your systems for newly discovered vulnerabilities soon after they are disclosed. It may not be a fully automated penetration test, but it certainly is like having an automated penetration tester watching over your systems! This feature is just as valuable to small businesses as it is to large enterprises as it mitigates the manual effort required to stay abreast of the latest threats. Protecting your systems is a far less daunting task when you have an automated tool monitoring between manual assessments.
A quality automated testing tool
Intruder uses the same underlying scanning engine that the big banks do, so you can enjoy high quality automated security checks, without the complexity. As part of our commitment to simplicity, we use a proprietary noise reduction algorithm which separates the informational from the actionable – so you can focus on what really matters to you and your business.
Intruder ensures that your systems are being continuously monitored for a spectrum of vulnerabilities, including web-layer security problems (such as SQL injection and cross-site scripting); infrastructure weaknesses (such as remote code execution flaws); and other security misconfigurations (such as weak encryption, and services that are unnecessarily exposed). A comprehensive list of all ~150,000 checks can be found in the Intruder portal.

Simple, seamless and effective
Scan results from other automated security testing tools can be challenging for those who are new to the world of security. Conversely, Intruder’s reports are easy to navigate, interpret and action — offering context for what could really happen if the issues we find were exploited. Moreover, the language we use deliberately strikes a careful balance between concise and coherent (for the less tech-savvy), but thorough enough that the team responsible for remediation have everything they need to ensure your systems remain secure.
For this reason, using Intruder could be compared to having had an automated penetration test — as what penetration testers often do is take the results from a vulnerability scanner, interpret them by filtering out the noise, and present them in a more readable way. Exactly what we do, but in an automated way.

Make continuous penetration testing a reality
Want to find weaknesses that evade the capabilities of automated tools? Intruder’s expert team proactively seek out weaknesses within the assets under the protection of the Vanguard solution — even closer to what you might want from an automated penetration test. Our team will analyze your scan results considering the business context of each vulnerability; reducing the number of false positives and finding dangerous vulnerabilities that are not apparent to automated scanners.
Using clever automation, we make it possible to do this year-round, so that automated penetration testing dream is one step closer to reality.

To achieve a robust level of security, we recommend performing both manual and automated penetration testing (more commonly known as vulnerability scanning). The automated tools provide continuity of security and speed whereas humans excel at finding more complex vulnerabilities, so you will benefit from combining the two. Read our blog to find out more about the differences.
The vulnerability scans can take anywhere from 15 minutes to several hours to complete, depending on your systems and their setups. Read our help article for more information.
There are many types of services on the market, such as network, web application, and automated penetration testing. If you’re not sure where to start, we’d recommend reading this article to find out which one is right for you. Or contact us for support, we would be more than happy to help!
Yes, with Intruder you can carry out authenticated web application scans. Perform thorough reviews of your modern web applications and websites, including single page applications (SPAs), to identify dangerous bugs which could have a severe business impact if not resolved.
In addition to fully automated scanning, we have a team of certified penetration testers at Intruder who can find complex issues beyond immediately available scan results as part of our Private Bug Bounty service.
The term “penetration testing” typically represents a manual process by which a cyber security professional attempts to uncover weaknesses in your IT infrastructure. In contrast, vulnerability scanning is automated, which means that you can run periodic scans on your systems as often as you need to, in order to avoid being breached. It is also worth noting that vulnerability scanning is often the first step performed by penetration testers to determine the overall state of your systems before proceeding with more in-depth manual reviews. Read our blog to find out more about the differences.













