Cyber Hygiene & Vulnerability Management Reporting
Gain full visibility of your security posture. Monitor your progress over time.
Easily share reports with customers, stakeholders and auditors.
Know and show what’s happening across your attack surface
Security leaders are under pressure to demonstrate not only how their security plans align with business goals but how effectively they are managing the risk across, their sometimes sprawling, attack surfaces. Intruder’s reporting and analytics capabilities make it easy for you to not only understand the current state of your attack surface but how your security posture has changed over time.

Trusted by thousands of companies worldwide































































See how easy vulnerability management reporting can be
See your security posture in real time
The dashboard highlights your threat level, critical issues and provides quick tips to improve your cyber hygiene score. Watch the activity feed to stay up-to-date on everything happening in your account including emerging threat scans, fixed issues, and discovery of new targets.

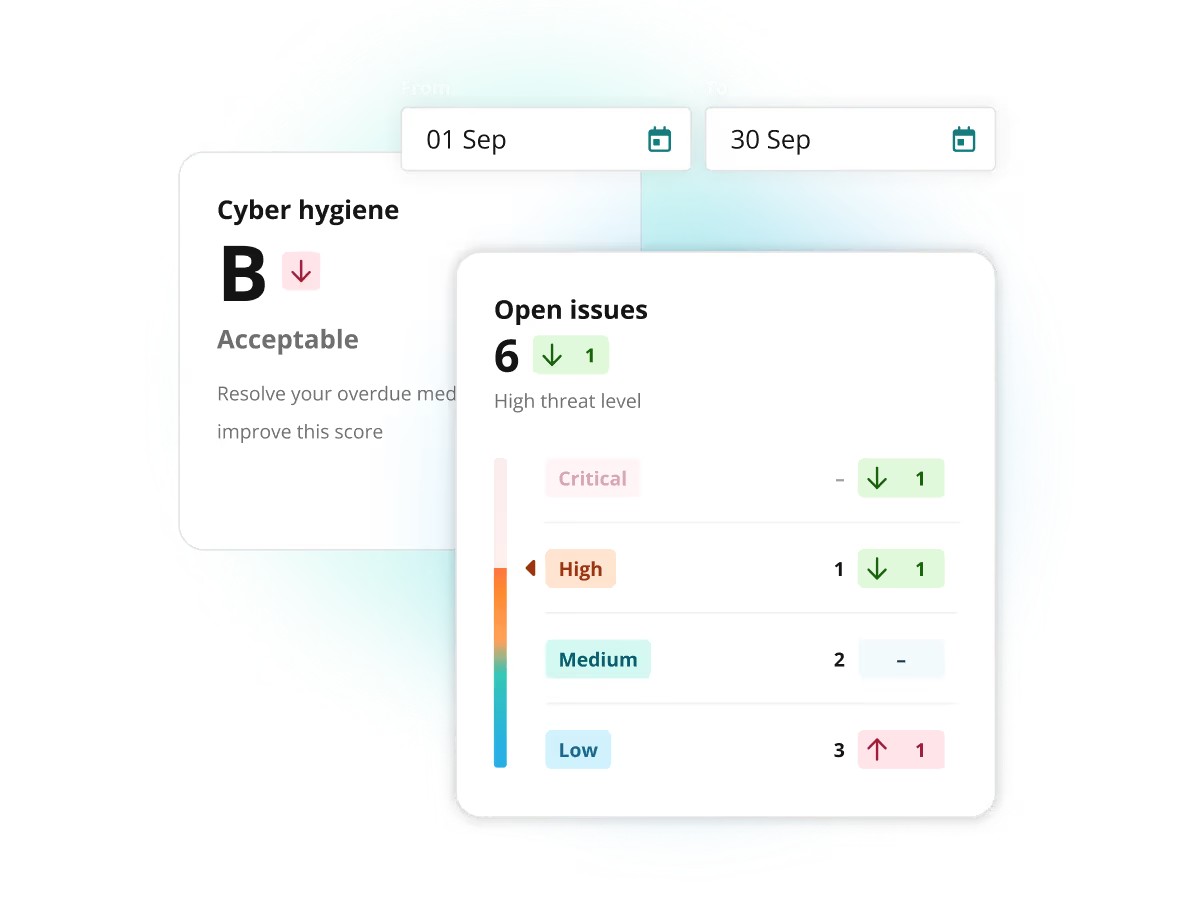
Improve security posture over time
Go further than a point-in-time understanding of your security posture, track the progress of your vulnerability management process over time with analytics. Compare time periods to get granular insight into your weaknesses, scans, and how your attack surface has changed over time.
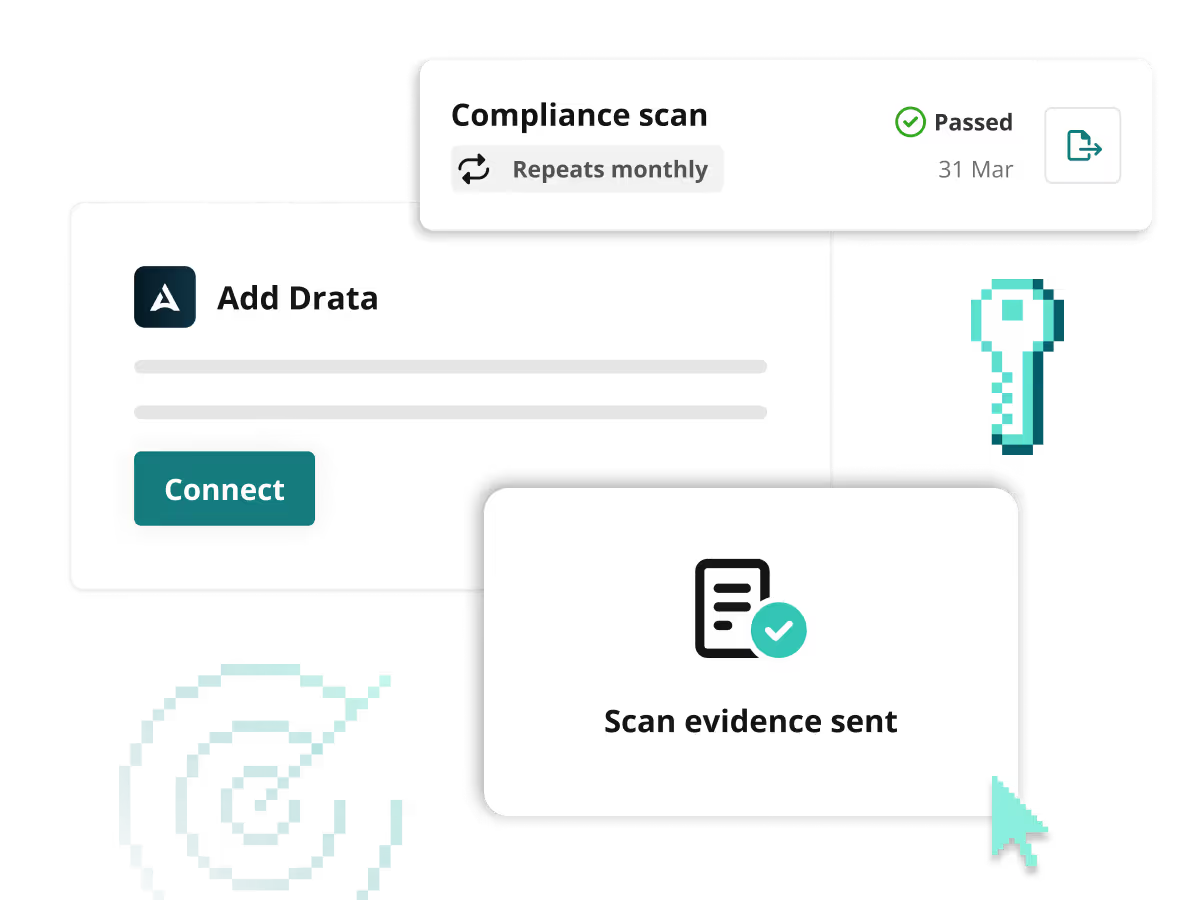
Save time with audit- ready reports
Access your latest scan directly from the dashboard, or filter down to specific targets or dates on the reports tab. Easily share reports with customers, stakeholders and auditors with the click of a button. Send vulnerability scanning evidence directly to compliance tools.
Stop threats in their tracks
With 65+ new vulnerabilities discovered daily, most businesses don't have the time or expertise to stay on top of them.
Intruder works to protect customers of all sizes from known emerging threats and discovered threats in the wild. So, when attackers are alerted to emerging vulnerabilities, we are too - and we are already checking your systems for them.

Read our reviews on G2.com









